CRYPTO ENCRYPTION TOOLS
Advanced Cryptographic Security Application
- This application offers a comprehensive set of professional cryptographic tools with secure key storage, designed for three types of users:
- Advanced users: Cryptography enthusiasts seeking reliable tools
- Students: Practical learning of cryptographic concepts
- Crypto system users: Administrators, DevOps and IT professionals
Features Overview
🔐 CRYPTO FAMILY
Fundamental cryptographic methods
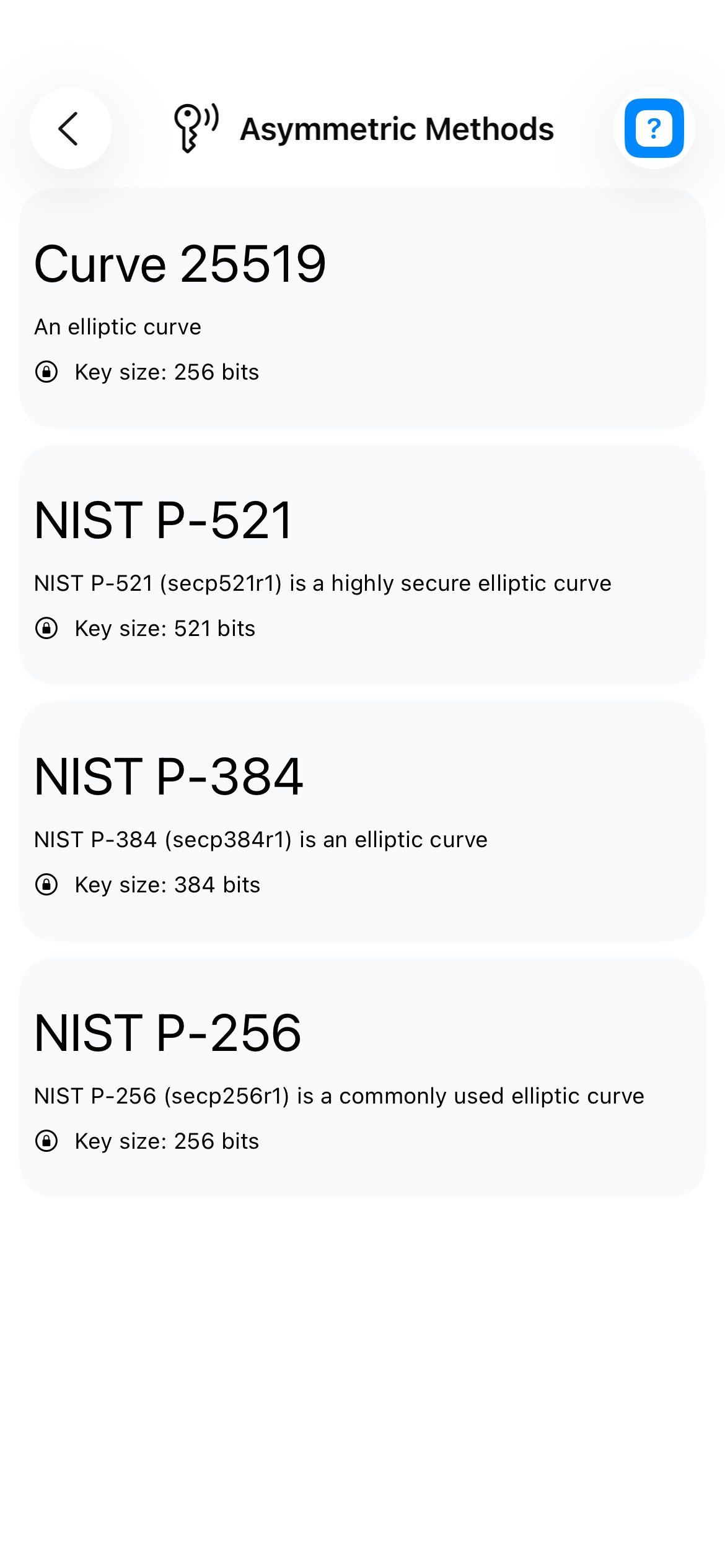
Asymmetric Methods
- Curve 25519 (256 bits) - Modern elliptic curve
- NIST P-521 (521 bits) - High security elliptic curve
- NIST P-384 (384 bits) - Secure elliptic curve
- NIST P-256 (256 bits) - Standard elliptic curve
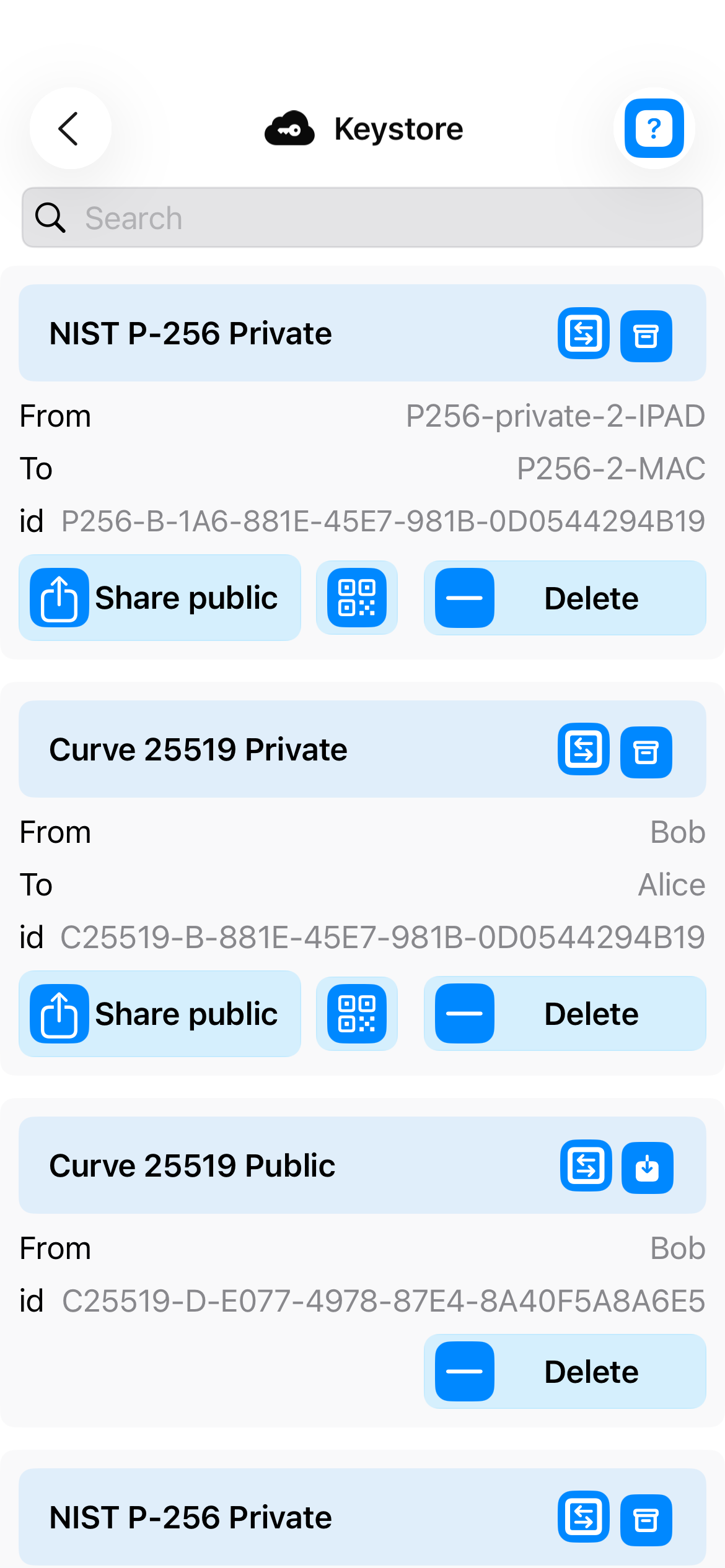
Secure Keystore
- Secure key storage with enhanced protection
- Centralized private/public key management
- Protection against side-channel attacks
Symmetric Encryption
- AES 256/192/128 - Advanced Encryption Standard
- ChaCha20-Poly1305 (256 bits) - Modern high-performance encryption
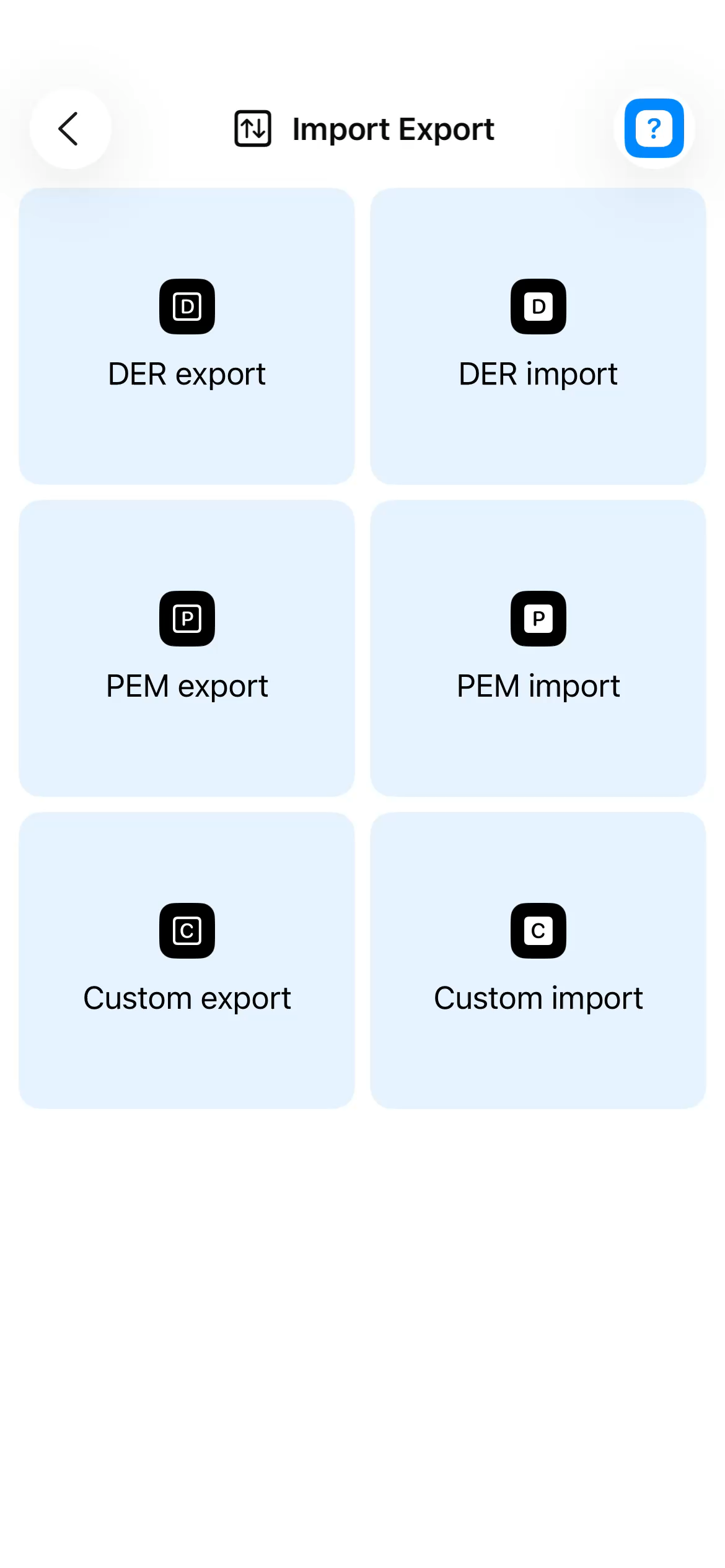
Import/Export
- DER Format - Binary import/export
- PEM Format - Standard textual import/export
- Custom Format - Proprietary formats
- Multi-platform compatibility
🛠️ TOOLS FAMILY
Practical cryptographic operations
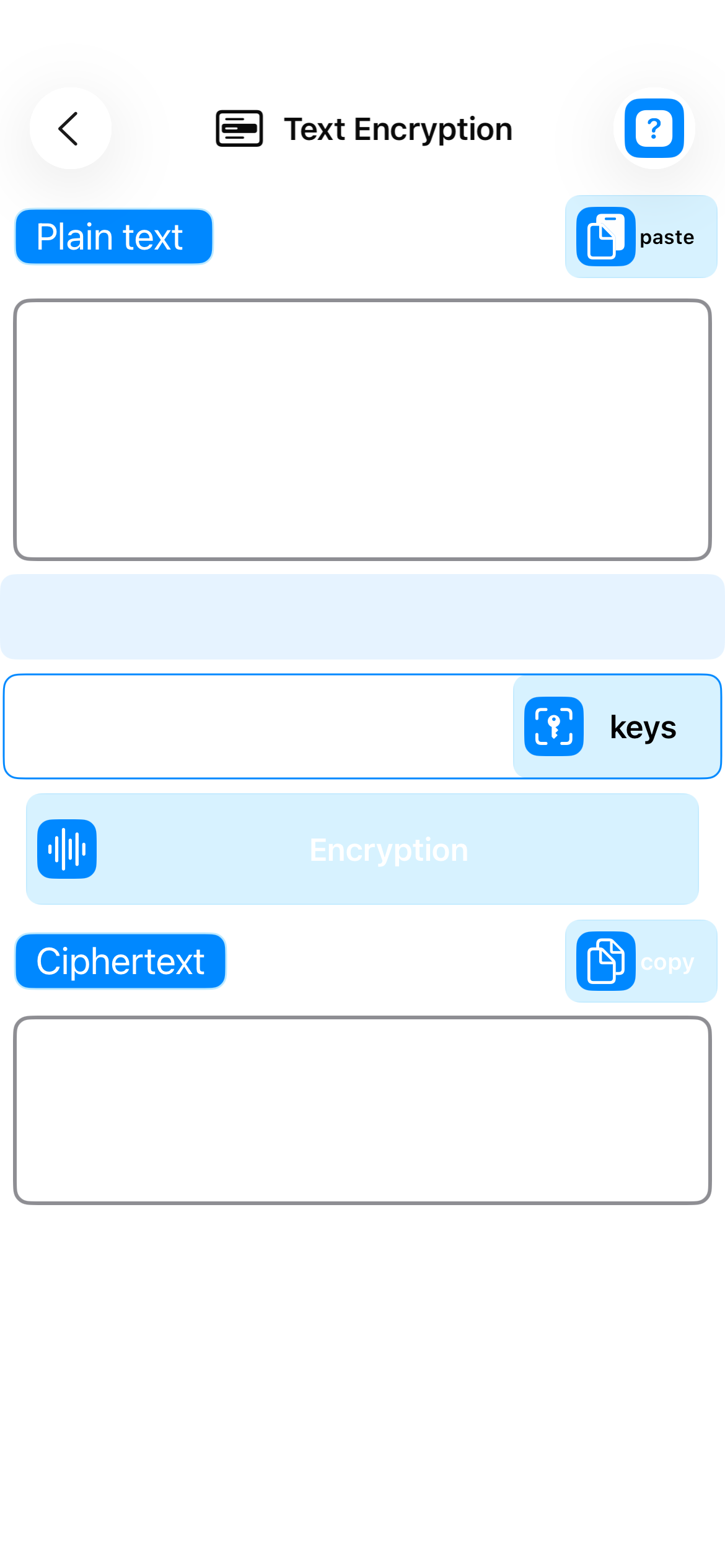
Data Encryption
- Text encryption - Messages and textual content
- Text decryption - Message recovery
- File encryption - Document protection
- File decryption - Document recovery
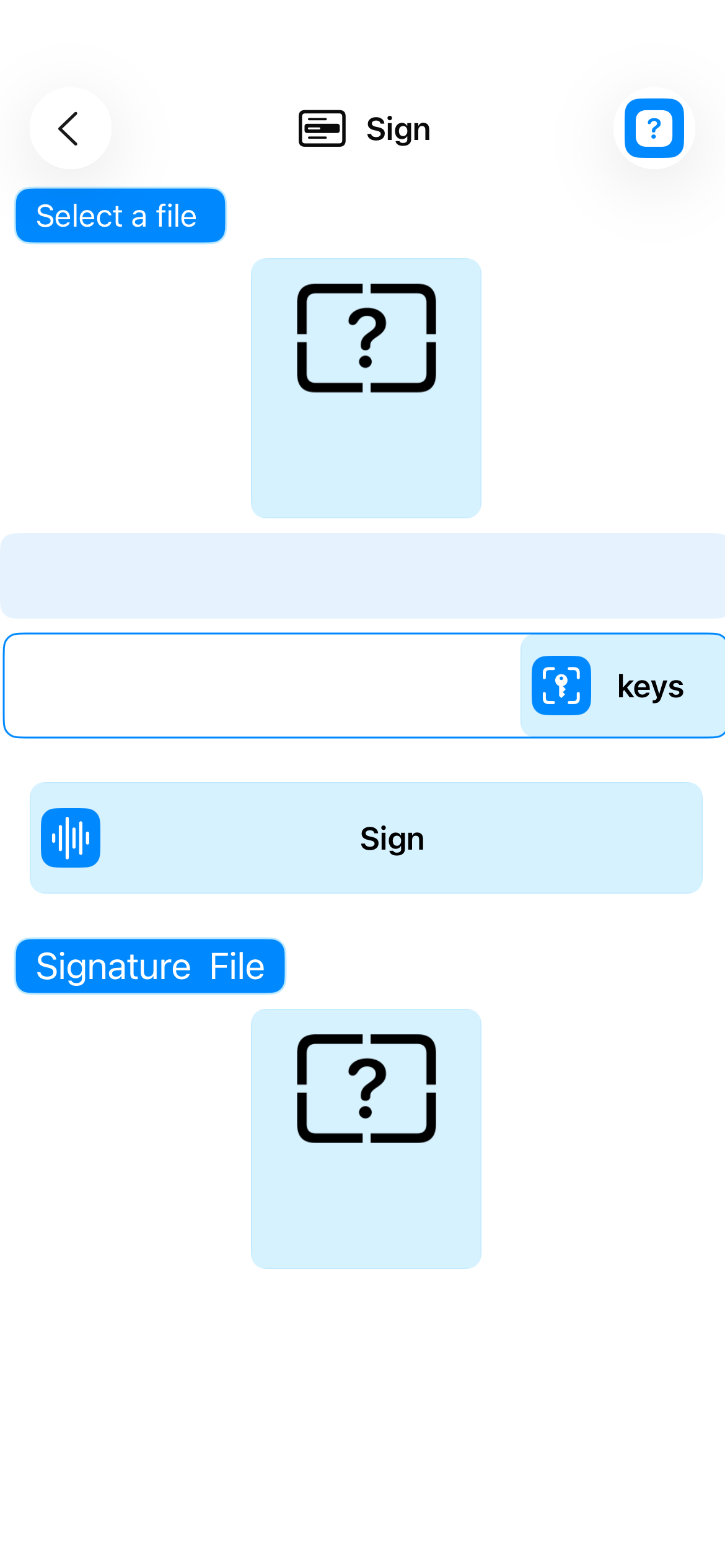
Digital Signature
- Document signing - Authentication and integrity
- Signature verification - Cryptographic validation
- Electronic signature standards support
⚡ ADVANCED TOOLS
Expert functionality
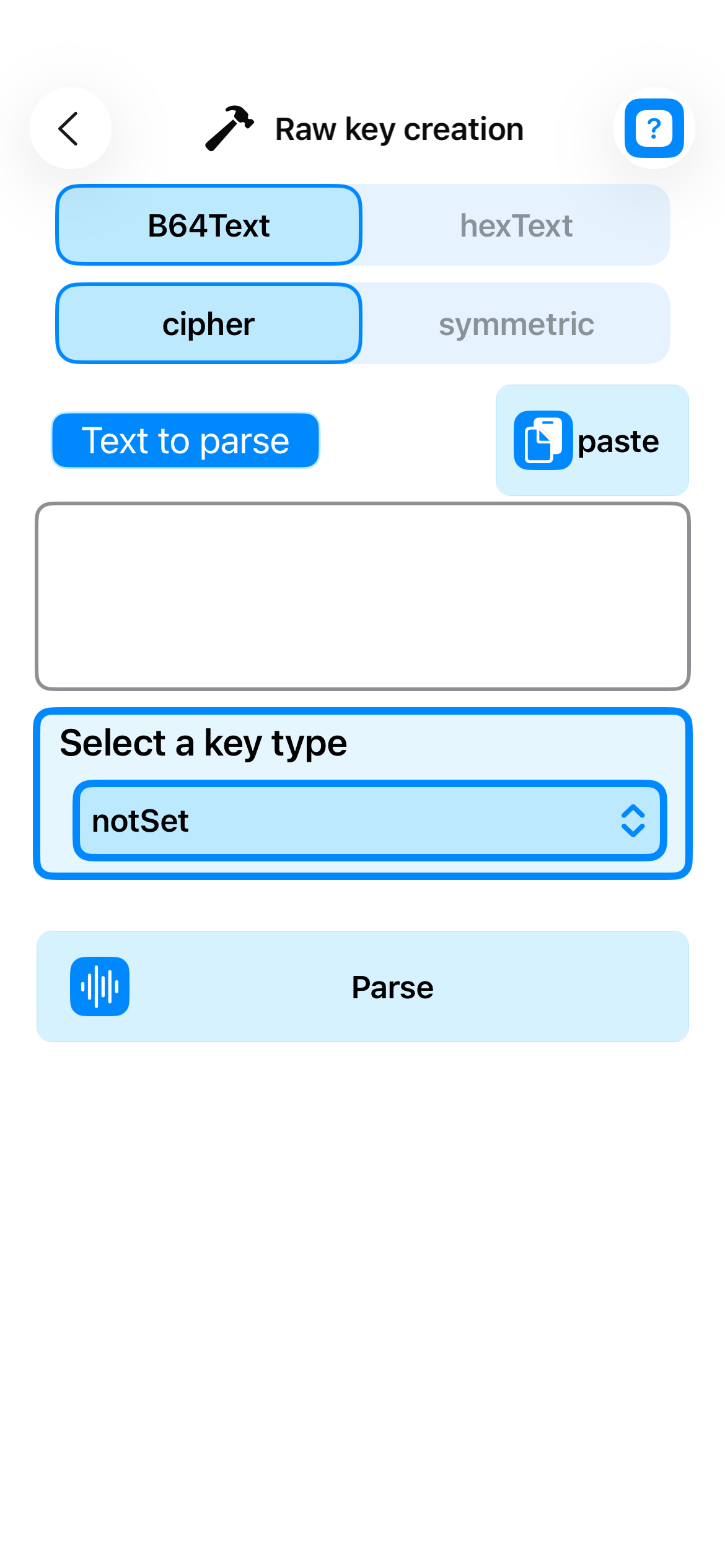
Advanced Key Creation
- Raw key generation - Custom creation
- Key import from Base64/Hexadecimal formats
- Secure generation with enhanced entropy
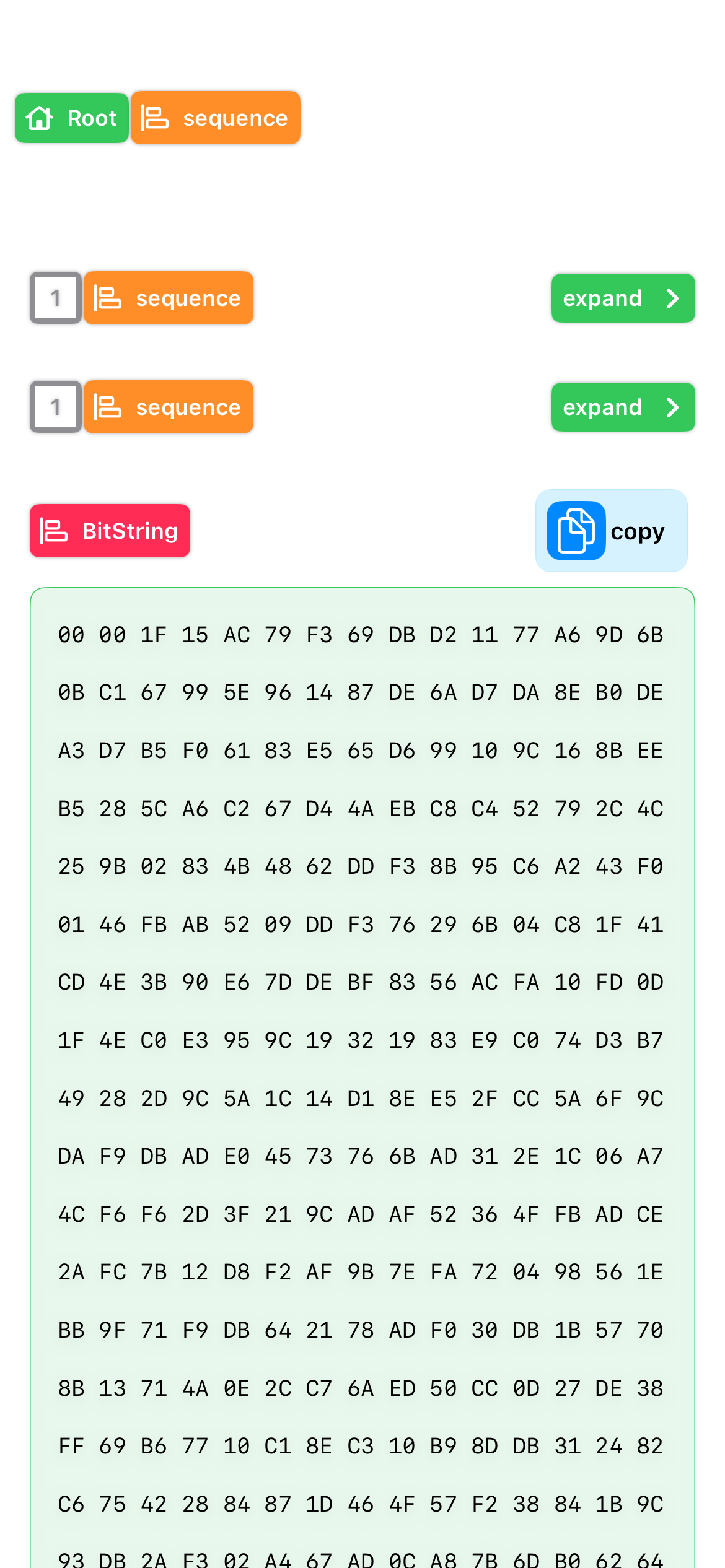
Cryptographic Analysis
- ASN.1 Analyzer - Cryptographic structure decoding
- X.509 Certificate parser
- Complex cryptographic format analysis
Hash Functions
- HASH - Cryptographic hash functions
- HMAC - Message authentication codes
- SHA-256/384/512 algorithm support

System Features
- Operation history
- Secure logging
- QR Code scanner
- Quick key/certificate import
- Advanced configuration
- Expert customization
🔒 ENHANCED SECURITY

Professional-grade Security
The application stands out for its professional-level security:
- Secure key storage in iOS/macOS Keychain
- Cryptographic data isolation
- Complete operation audit trail
- Industry standards compliance (FIPS, Common Criteria)

